In the world of 2026 cybersecurity, the internet is no longer a private space—it is a public highway where every packet of data you send is a target. To stay invisible, you don't just need a new public IP; you need a cryptographic fortress. A VPN tunnel is that fortress. It transforms your readable data into uncrackable noise, ensuring that even if a hacker intercepts your network path, they see nothing but gibberish. Understanding how VPN tunnels encrypt data is the key to mastering your digital sovereignty.
"In my 20 years of auditing corporate security infrastructures, I've seen many people mistake 'VPN usage' for 'VPN security.' A tunnel is only as strong as its handshake protocol. If your VPN doesn't implement Perfect Forward Secrecy (PFS), your old public data could be decrypted in the future. Encryption isn't just about hiding; it's about making time work against the attacker."
1. The Anatomy of a VPN Tunnel: Logical vs. Physical
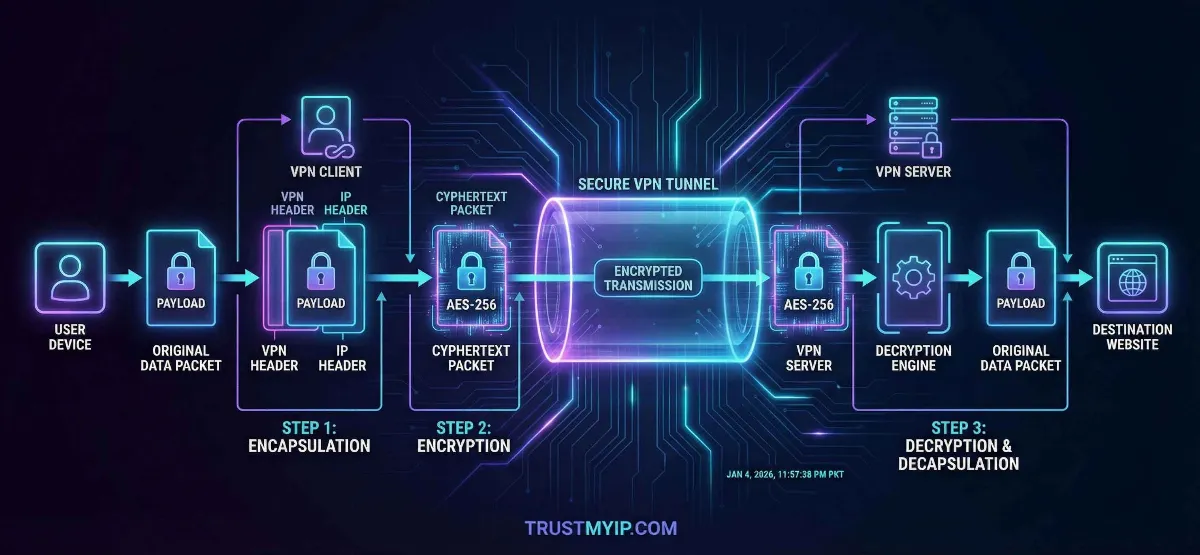
A VPN tunnel isn't a physical cable; it is a logical connection created over the existing infrastructure of your ISP (Comcast, Verizon, or Starlink). It works by wrapping your original data packets inside a new, encrypted packet—a process known as Encapsulation.
Layer 3 Network Isolation
Unlike a standard proxy that works at the application level, a VPN operates at the Network Layer (OSI Layer 3). This means it encrypts everything from your browser traffic to your background Windows or Mac system updates. By doing so, it effectively masks your network identity from the bottom up.
Step 0: Identity Check. Before tunneling, see what you're exposing. Use our IP Identity Tool to see your raw Public IP and ISP details.
2. Step-by-Step: How Your Data is Encrypted
Encryption is a multi-stage forensic process that happens in milliseconds. Here is the SOP (Standard Operating Procedure) of a secure 2026 VPN tunnel.
Phase 1: The Secure Handshake
Before any data is sent, your device and the VPN server must agree on how to talk. They use Asymmetric Encryption (Public/Private Keys) to securely exchange a "Session Key." This is usually done through the Diffie-Hellman key exchange protocol.
Phase 2: Symmetric Encryption (The Heavy Lifting)
Once the handshake is complete, the VPN switches to Symmetric Encryption (like AES-256 or ChaCha20) because it is much faster and provides higher throughput. Your public data is now transformed into ciphertext using the agreed-upon session key.
Integrity Hashing (HMAC)
To ensure a hacker hasn't modified your encrypted data, the VPN adds a digital signature (Hash). If the hash doesn't match on the other end, the packet is dropped instantly.
Authentication
The server verifies your authorized user credentials to ensure you have the right to join the VPN tunnel.
3. Protocols: The Engines of the VPN Tunnel
In 2026, the protocol you choose determines both your internet speed and your level of privacy. Not all tunnels are built the same.
| Protocol | Encryption Algorithm | Best For |
|---|---|---|
| WireGuard | ChaCha20 | Gaming & Hypixel Stability |
| OpenVPN | AES-256 | Strict Corporate Security |
| IKEv2/IPSec | AES-GCM | Mobile iPhone/Android Roaming |
Want to know which protocol is best for your region? Check our VPN vs. Proxy Verdict.
4. Tunneling Through Space: VPNs on Starlink
Running a VPN on Starlink introduces unique technical constraints due to Carrier-Grade NAT (CGNAT) and satellite handoffs.
The Latency Factor
Because a VPN tunnel adds extra headers to every packet, your Starlink internet speed might decrease by 10-15%. However, it solves the problem of Anycast Routing issues that can sometimes block satellite users from certain sites. For a full audit, read our Starlink IP Architecture Guide.
5. Why VPN Tunnels Fail: Troubleshooting Leaks
Even the strongest encryption can't save you if your network identity leaks through a "side door."
- DNS Leaks: If your browser bypasses the tunnel to ask your ISP for DNS Resolution, they know exactly which site you are visiting. Use our DNS Auditor to check.
- IP Address Conflict: If your VPN tunnel subnet matches your local LAN IP (e.g., 192.168.1.1), the tunnel will crash. Read our IP Conflict Resolution Manual.
- WebRTC Exposure: Modern browsers can reveal your real private IP even inside a VPN. Run our Forensic Proxy Leak Test to verify your stealth.
6. Beyond the Tunnel: Does a VPN Mask Your MAC Address?
A common misconception is that a VPN hides everything. It does not. While it masks your Public IP, your MAC Address is still visible to your local router and any apps with system-level access.
"Identity in 2026 is a multi-layered stack. A VPN protects your public data at Layer 3, but your hardware identity (Layer 2) remains. To stay truly anonymous, you must understand the Difference Between MAC and IP and how to manage your network documentation."
Conclusion: The Future of Encrypted Networking
Mastering how VPN tunnels encrypt data is the first step toward true cybersecurity hygiene in 2026. From the initial Diffie-Hellman handshake to the daily stability of WireGuard, these cryptographic layers protect our most sensitive information from exposure. By auditing your network path for leaks and managing your authorized user protocols, you ensure that your digital life remains private, resilient, and ready for the challenges of a connected world.
Is Your Tunnel Secure?
Encryption is useless if your IP is leaking. Use our forensic toolkit to audit your DNS health, check for WebRTC leaks, and verify your 2026 IP reputation in one click.