In the hyper-scaled digital landscape of 2026, the direct connection between a user and a server is becoming a relic of the past. As corporate security demands rise and global networks face unprecedented traffic, the proxy server has emerged as the most critical gatekeeper of the internet. Understanding the role of proxy servers in networking is no longer just for system administrators—it is essential for anyone looking to optimize throughput, mask their network identity, or protect their public data. From simple caching to complex SSL termination, proxies are the invisible engines driving modern connectivity.
"In my 20 years of building global networks, I've seen proxies evolve from simple storage caches into sophisticated security hubs. A proxy isn't just a 'middleman'; it is a programmable logic point on the network path. If you are not leveraging proxies at both the Transport (Layer 4) and Application (Layer 7) levels, your network is inherently exposed to latency and forensic detection."
1. Core Mechanics: How Proxy Servers Function at the OSI Layers
At its most fundamental level, a proxy server is an intermediary system that separates the sender from the receiver. When you request a resource from the World Wide Web, the proxy intercepts the request, evaluates it against a security policy, and then acts on your behalf.
Layer 4 vs. Layer 7 Proxying
Modern proxies operate at different stages of the TCP/IP stack. A Layer 4 proxy works at the transport level, managing traffic based on numeric IP and port numbers. In contrast, a Layer 7 proxy—often called an Application Proxy—can inspect the actual content of the request, such as HTTP headers and cookies, to make intelligent routing decisions.
Step 0: Identity Verification. Before exploring proxy roles, check your own exposure. Use our IP Identity Tool to see what information your current network is leaking.
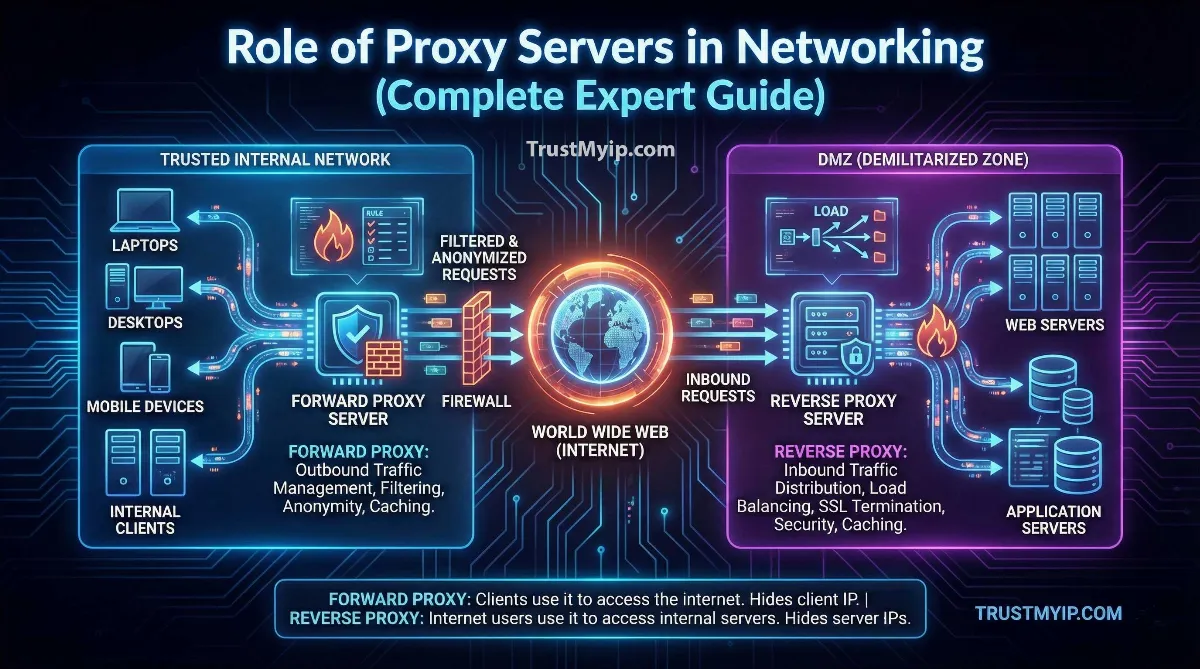
2. Forward vs. Reverse Proxies: Mapping the Traffic Flow
The most important distinction in proxy server architecture is the direction of the traffic flow. Each serves a unique purpose in network documentation.
The Forward Proxy (Client-Side)
Acts on behalf of the client. It is used to bypass geo-blocks, hide your public IP, and filter internal employee traffic. If you want to access unreleased features, read our guide on Changing IP for Early Access.
The Reverse Proxy (Server-Side)
Acts on behalf of the server. It handles load balancing, SSL termination, and caching. Websites like Facebook and Google use massive reverse proxy arrays to manage millions of authorized users.
3. Strategic Roles: Why Modern Networks Depend on Proxies
Proxies are versatile tools that address multiple technical constraints simultaneously. In 2026, their roles have expanded into four primary domains.
Role A: Enhanced Security & Filtering
Proxies act as a buffer. By inspecting traffic before it reaches the internal network, they can block malware and prevent DDoS attacks. This is a cornerstone of corporate security. If you suspect your IP has been flagged, check out our IP Blockade Forensic Guide.
Role B: Content Caching & Performance
By storing local copies of popular public data, proxies reduce the need for repeat trips to the origin server. This lowers latency and significantly boosts the perceived internet speed for end-users.
Role C: Privacy & Anonymity
A proxy replaces your real numeric IP with its own. This is vital for users in restricted regions. However, choosing the right type of proxy is critical. Read our VPN vs. Proxy Comparison to see which fits your network identity.
4. Advanced Roles: SSL Termination and Load Balancing
In 2026, the proxy is the workhorse of high-availability infrastructure, handling complex tasks that would otherwise overwhelm an origin server.
| Advanced Role | Mechanism | Primary Benefit |
|---|---|---|
| SSL Termination | Decodes HTTPS at the Proxy | Reduces Server CPU Load |
| Load Balancing | Distributes Requests | Eliminates Single Points of Failure |
| Anycast Routing | Geo-Proximity Rerouting | Minimum Latency |
5. Proxies in Specialized Networks: IoT and Satellite
Specialized networks like Starlink use proxies to manage Carrier-Grade NAT (CGNAT) and satellite handoffs. In these environments, the proxy ensures that your network path remains stable even as the physical satellite moves across the sky.
Satellite Networking Context:
On satellite links, proxies help overcome high RTT (Round Trip Time) by pre-fetching data. For a deeper look at satellite identity, read our Starlink IP Logic Guide.
6. Troubleshooting: When Proxies Cause Network Friction
While proxies offer immense benefits, improper configuration can lead to technical constraints like IP conflicts or broken DNS Resolution.
- IP Address Conflicts: If two proxies attempt to use the same private IP on a local subnet, the connection will drop. Fix this using our Conflict Resolution Manual.
- DNS Leaks: A poorly configured proxy may leak your real DNS Resolution requests. Use our Global DNS Auditor to check for exposure.
- MAC Identity: Proxies often mask your IP but leave your MAC Address exposed in local logs. Learn the Difference Between MAC and IP.
Conclusion: The Strategic Imperative of Proxy Servers
The role of proxy servers in networking is one of mediation and empowerment. By acting as a sophisticated network identity buffer, proxies allow organizations and individuals to navigate the World Wide Web with higher speed, greater security, and total privacy. Whether you are leveraging a residential proxy for market research or deploying a reverse proxy for corporate security, mastering this technology is the first step toward a resilient digital future. In 2026, the proxy is not just a tool—it is the very backbone of a secure and optimized network.
Are You Fully Protected?
Don't trust your proxy blindly. Use our forensic toolkit to audit your DNS health, detect Proxy leaks, and verify your 2026 IP reputation in one click.