In the competitive landscape of modern web infrastructure, residential proxies have emerged as the gold standard for legitimate data collection operations. Unlike datacenter proxies that scream "bot activity" to sophisticated anti-scraping systems, residential IPs originate from real household internet connections assigned by Internet Service Providers (ISPs), making web traffic appear indistinguishable from genuine user behavior. This authenticity factor has transformed residential proxy networks into mission-critical infrastructure for enterprises conducting market research, price monitoring, and competitive intelligence.
Understanding what is a residential proxy and why do you need one requires examining both the technical architecture enabling this level of anonymity and the specific business use cases where residential IPs deliver measurable ROI. From bypassing geographic restrictions to avoiding IP bans on high-security target sites, residential proxies solve the fundamental challenge that datacenter infrastructure cannot: making automated traffic look human. Whether you're scaling a web scraping operation, managing multiple social media accounts, or verifying advertisements across regions, this comprehensive guide reveals why residential proxy networks have become non-negotiable for data-driven businesses in 2026.

"After architecting proxy infrastructures for Fortune 500 data operations, I've witnessed the arms race between web scraping technologies and anti-bot defenses. The decisive advantage of residential proxies isn't just their legitimate IP origin, it's the distributed nature of the network spanning thousands of ISPs and geographies. When Cloudflare or Akamai analyze traffic patterns, they see what appears to be thousands of individual users, not a single entity making coordinated requests. That fundamental camouflage makes residential IPs irreplaceable for production-scale data collection."
The Quick Resolution: Residential Proxy Essentials
A residential proxy routes your internet traffic through real home IP addresses assigned by consumer ISPs, making requests appear as legitimate user activity rather than automated bot traffic. You need residential proxies to bypass sophisticated anti-scraping systems, access geo-restricted content, avoid IP bans, and conduct anonymous market research without triggering detection. They are essential for web scraping, ad verification, price monitoring, and any operation requiring high-volume data access from websites with advanced bot protection.
1. What is a Residential Proxy? The Technical Foundation
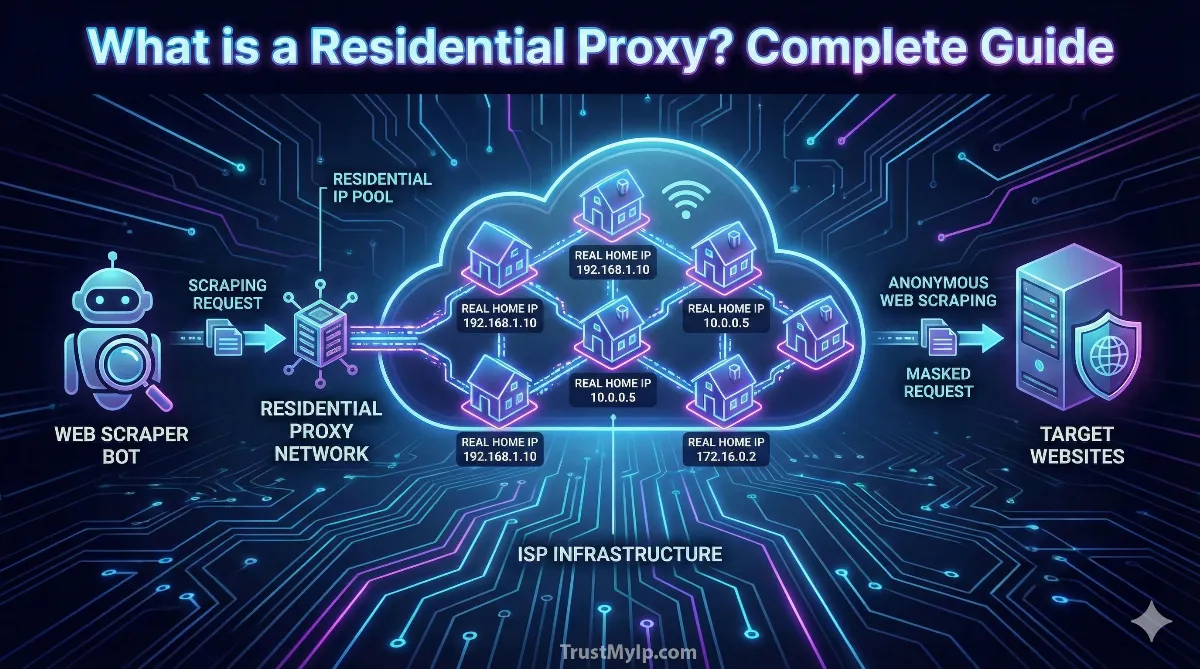
A residential proxy is an intermediary server that assigns you an IP address originating from a genuine residential internet connection provided by an ISP like Comcast, Verizon, or AT&T. These IPs belong to real physical devices in actual homes, apartments, and businesses connected via cable, fiber, DSL, or mobile broadband networks.
The Fundamental Difference: Real IPs vs Datacenter IPs
When you browse the web normally, your ISP assigns your home router a residential IP address that identifies your connection to the broader internet. This IP carries metadata indicating it belongs to a consumer network rather than a commercial hosting environment. In contrast, datacenter proxies use IP addresses from cloud providers like AWS, Azure, or DigitalOcean, which websites can instantly identify as non-residential through ASN (Autonomous System Number) lookups and WHOIS databases.
How Residential Proxy Networks Are Built
Residential proxy providers partner with software developers who integrate internet-sharing applications into free VPN services, browser extensions, or mobile apps. Users who install these applications consent to share their unused bandwidth in exchange for free access to the primary service. When someone purchases residential proxy access, their traffic routes through this distributed network of opted-in residential devices. Ethical providers like Bright Data ensure full transparency and user compensation, while unethical operators may hijack IP addresses through malware or botnets. Learn about IP infrastructure in our guide to the strategic role of proxy servers in networking.
2. How Residential Proxies Work: The Request Flow
Understanding the technical workflow reveals why residential proxies achieve superior anonymity compared to other proxy types. The multi-hop architecture ensures your real identity remains hidden while presenting authentic residential credentials to target websites.
Residential Proxy Connection Flow
Step 1: You send a request to access a target website from your device or scraping script.
Step 2: The request routes to the residential proxy provider's gateway server.
Step 3: The gateway assigns you a residential IP address from the proxy pool based on your location preferences.
Step 4: Your traffic forwards through the selected residential device (a real home connection).
Step 5: The target website receives the request appearing to originate from the residential IP, complete with legitimate ISP routing and geographic metadata.
Step 6: The website's response travels back through the same path, reaching your device through the residential proxy.
Result: The website sees only the residential IP address, while your real identity and location remain completely hidden.
The key technical advantage is that residential IPs pass all standard verification checks websites use to identify bots, including reverse DNS lookups, ASN verification, and behavioral fingerprinting. Since the traffic genuinely originates from consumer ISP infrastructure, detection systems classify it as legitimate user activity. Compare this to VPN services in our VPN versus proxy comparison guide.
3. Residential Proxies vs Datacenter Proxies: The Critical Distinctions
Choosing between residential and datacenter proxies fundamentally impacts your operation's success rate, cost structure, and detection risk profile. Understanding the tradeoffs guides infrastructure decisions.
| Characteristic | Residential Proxies | Datacenter Proxies |
|---|---|---|
| IP Source | Real ISP-assigned home addresses | Cloud hosting providers (AWS, Azure, GCP) |
| Detection Risk | Extremely Low (appears as real users) | High (easily identified via ASN) |
| Cost | $5-15 per GB or $300-800/month for pools | $1-3 per GB or $50-200/month |
| Connection Speed | Variable (depends on home connections) | Very Fast (optimized data centers) |
| IP Pool Size | Millions of IPs across global ISPs | Thousands to tens of thousands |
| Best Use Case | Sites with strong anti-bot protection | High-speed bulk data transfer tasks |
The cost difference reflects the infrastructure complexity. Datacenter providers control their own IP ranges and can provision thousands of addresses cheaply. Residential proxy operators must compensate individual device owners and manage a distributed network spanning multiple ISPs, resulting in higher operational costs passed to customers. For web scraping high-value targets with sophisticated bot detection, the premium for residential IPs delivers measurable ROI through higher success rates and fewer blocks. Check your current IP type with our IP address lookup tool.
4. Why You Need Residential Proxies: Business Use Cases
Residential proxies solve specific operational challenges that justify their premium pricing. Understanding which use cases demand residential infrastructure versus cheaper alternatives ensures optimal resource allocation.
Mission-Critical Residential Proxy Applications
- • Web Scraping Protected Sites: E-commerce platforms like Amazon, Shopify, and eBay deploy machine learning anti-bot systems that flag datacenter IPs instantly. Residential proxies bypass these defenses by presenting legitimate consumer connections.
- • Price Monitoring & Competitive Intelligence: Track competitor pricing strategies across geographic markets without triggering rate limits. Residential IPs rotate through different ISPs to distribute requests naturally.
- • Ad Verification: Agencies verify client advertisements display correctly across regions and aren't victims of ad fraud. Residential proxies from target geographies show actual user experiences.
- • Social Media Management: Manage multiple Instagram, Twitter, or Facebook accounts without platform detection linking them to a single operator. Each account appears to access from different residential locations.
- • Sneaker & Limited Edition Purchasing: Retail sites limit purchases per IP to prevent bot scalping. Residential proxy networks enable multiple simultaneous purchases appearing as individual shoppers.
- • SEO & SERP Monitoring: Check search engine rankings from different locations without personalization bias. Google penalizes datacenter IPs with CAPTCHAs but treats residential connections normally.
The common thread across these use cases is that target websites actively combat bot activity using IP reputation databases, behavioral analysis, and device fingerprinting. Residential proxies defeat these countermeasures by providing genuinely diverse traffic sources that blend with organic user activity. For geo-restriction bypassing, see our guide on best residential proxy for bypassing geo-blocks.
5. Static vs Rotating Residential Proxies: Choosing the Right Type
Residential proxy services offer two operational modes with distinct characteristics suited to different workflows. Understanding the architecture and cost implications guides purchasing decisions.
Static Residential Proxies
Static residential proxies assign you a fixed IP address from the residential pool that persists for the duration of your session or subscription period. This consistency makes them ideal for operations requiring stable connections like managing social media accounts, maintaining authenticated sessions, or conducting long-running monitoring tasks. The limitation is that using the same IP repeatedly may eventually trigger rate limits on target sites, though the residential origin provides significant protection compared to datacenter alternatives.
Rotating Residential Proxies
Rotating residential proxies automatically change your assigned IP address on every request or at configurable time intervals, distributing your traffic across thousands of residential connections. This rotation pattern perfectly mimics organic traffic where each user comes from a unique IP, making detection nearly impossible even at massive scale. Rotating proxies excel at high-volume web scraping, SERP monitoring, and any operation where request volume from a single IP would raise flags. The tradeoff is slightly higher complexity managing session persistence when applications require maintaining state across requests. Learn about network architecture in our Anycast routing infrastructure guide.
6. Geographic Targeting: Accessing Location-Specific Content
One of the most powerful features of residential proxy networks is granular geographic targeting, enabling you to access content as if physically located anywhere in the world. This capability unlocks market research and competitive intelligence previously impossible to collect at scale.
Geographic Targeting Capabilities:
- • Country-Level Targeting: Select residential IPs from specific countries to bypass regional content restrictions or access local pricing data.
- • City-Level Precision: Premium providers offer city-specific targeting for applications like local SEO monitoring or regional market research.
- • ISP Selection: Advanced targeting allows choosing specific internet service providers to test how content appears to customers of particular carriers.
- • ASN Targeting: For technical operations, some providers enable selection by Autonomous System Number to emulate traffic from specific network operators.
Geographic diversity also provides operational resilience. If one region's IP pool experiences blocking or degraded performance, you can instantly pivot to alternative locations without interrupting operations. This flexibility proves crucial for mission-critical data collection where downtime directly impacts revenue. Verify geographic accuracy with our IP geolocation lookup tool.
7. Ethical Sourcing: How Legitimate Providers Build Proxy Networks
The residential proxy industry faces ethical scrutiny over how IP addresses are obtained. Understanding sourcing practices helps you select providers that operate transparently and legally while avoiding networks built on compromised devices or malware distribution.
Ethical Residential Proxy Sourcing Requirements:
- • Explicit User Consent: Device owners must actively opt-in to sharing their internet connection, with clear disclosure of how their bandwidth will be used.
- • Compensation Mechanisms: Legitimate providers compensate users through free premium features, cash payments, or reward points for sharing their connection.
- • Transparent Applications: The software facilitating connection sharing should clearly identify itself rather than bundling surreptitiously with unrelated applications.
- • User Control: Participants must be able to pause or disable connection sharing at will, and uninstall the application cleanly without residual network access.
- • Privacy Protection: Ethical providers implement encryption and traffic isolation ensuring proxy users cannot access device owners' personal data or local network resources.
Unethical operators build proxy networks by embedding connection-sharing code in pirated software, browser hijackers, or malware that infects devices without consent. These botnet-sourced proxies carry significant legal and security risks for customers. If a provider cannot clearly explain their sourcing methodology or avoids questions about user consent, that's a critical red flag indicating potentially compromised infrastructure. For proxy security, read our guide on whether it's safe to use free proxies.
8. Setting Up Residential Proxies: Integration Methods
Implementing residential proxies requires configuring your applications or scripts to route traffic through the proxy network. Most providers support multiple integration methods accommodating different technical environments and use cases.
Common Integration Methods
HTTP/HTTPS Proxy Protocol: Configure applications to route web traffic through proxy hostname and port. Works with browsers, web scraping frameworks like Scrapy or Puppeteer, and HTTP client libraries.
SOCKS5 Protocol: More flexible tunneling protocol supporting any traffic type, not just HTTP. Required for applications that need proxy support at the network layer rather than application layer.
API Integration: Enterprise providers offer REST APIs for programmatic control, enabling dynamic IP rotation, geographic selection, and session management from your code.
Browser Extensions: Simple setup for manual browsing tasks through drag-and-drop configuration, though less suitable for automation at scale.
SDK/Libraries: Native integrations for popular frameworks automate proxy rotation and error handling without custom code.
The technical implementation varies by provider but typically involves authenticating with username/password credentials or API keys, then configuring your application to route requests through the proxy endpoint. Advanced setups implement retry logic to handle temporary connection failures and session management to maintain state when using rotating proxies. Test your proxy configuration with our proxy detection tool.
9. Legal Considerations: When and How to Use Residential Proxies
Residential proxies themselves are legal tools, but their use must comply with website terms of service, data protection laws, and computer fraud statutes. Understanding the legal boundaries prevents violations that could result in civil liability or criminal prosecution.
- Terms of Service Compliance: Many websites explicitly prohibit automated data collection in their ToS. Using proxies to circumvent these restrictions may constitute breach of contract, exposing you to civil lawsuits.
- Computer Fraud Laws: The Computer Fraud and Abuse Act in the US criminalizes unauthorized access to computer systems. Courts have ruled that violating ToS combined with technical circumvention measures like proxies can meet this threshold.
- Data Protection Regulations: Scraping personal information may violate GDPR, CCPA, or other privacy laws depending on the data type and your intended use. Consult our IP tracing legality guide.
- Ethical Provider Selection: Using proxies sourced from malware or unauthorized device access may implicate you in criminal conspiracy even if you weren't aware of the sourcing method.
- Acceptable Use Policies: Reputable proxy providers maintain strict acceptable use policies prohibiting illegal activities. Violating these terms results in account termination and potential reporting to authorities.
10. Choosing a Residential Proxy Provider: Evaluation Criteria
Selecting the right residential proxy provider requires evaluating technical capabilities, pricing structure, ethical practices, and support quality. The wrong choice leads to operational failures, wasted budget, and potential legal exposure.
Critical Evaluation Checklist
- IP Pool Size & Quality: Millions of IPs distributed across multiple ISPs and geographies provide better rotation and reduce detection risk compared to smaller pools.
- Geographic Coverage: Verify the provider offers IPs in your target markets with city-level precision if needed for local content access.
- Success Rate Metrics: Request data on connection success rates and average response times for your target websites before committing to a contract.
- Pricing Transparency: Understand whether billing is per GB of bandwidth, per request, or fixed monthly pools. Watch for hidden overage fees or minimum commitments.
- Protocol Support: Ensure compatibility with your technical stack including HTTP(S), SOCKS5, and any framework-specific requirements like Selenium or Puppeteer integration.
- Ethical Sourcing Verification: Request detailed information about how the provider acquires residential IPs and whether users explicitly consent and receive compensation.
- Customer Support: Test responsiveness and technical knowledge before purchasing. Production operations require quick resolution of connectivity issues.
Conclusion: Why Residential Proxies Are Non-Negotiable Infrastructure
Understanding what is a residential proxy and why do you need one comes down to recognizing that modern websites deploy sophisticated anti-bot systems specifically designed to identify and block datacenter IP traffic. Residential proxies defeat these defenses by routing your requests through legitimate consumer internet connections that appear identical to organic user activity. Whether conducting competitive intelligence, market research, ad verification, or price monitoring, residential proxy infrastructure